
Contents
Countering Ransomware Financing
Nature of Ransomware
Ransomware is malware used by criminals to block access to data or systems, demanding a ransom for release. It involves methods like data encryption, data exfiltration, and operational disruption, often threatening to publish the victim’s data.
Growth and Impact
Ransomware attacks have significantly increased in number and scale, mainly for profit. Ransom payments surged fourfold in 2020 and 2021 compared to 2019. Despite a potential decline in 2022, the financial impact remains high.
Consequences and Techniques
Attacks disrupt governments, institutions, businesses, and individuals, sometimes affecting national security and healthcare. Criminals have refined their techniques for more profitable and successful attacks, continuing the threat of illicit financial flows.
Ransom Payments in Virtual Assets
Ransoms are almost exclusively demanded in virtual assets, using virtual asset service providers (VASPs) for payment and laundering, converting the proceeds to fiat currency.
Financial Flows in Ransomware and Laundering Techniques
Involvement of Financial Institutions and Third Parties
Ransomware financial flows often involve multiple traditional financial institutions and Virtual Asset Service Providers (VASPs). Cyber insurance companies, incident response firms, and cybersecurity companies may also partake in the response to attacks, including the payment process.
Use of Virtual Assets
While virtual assets are the primary medium for ransomware payments, the overall financial flows involve traditional financial institutions, VASPs, and other third parties.
Anonymity Enhancing Techniques in Laundering
- Wallet Addresses: Attackers demand virtual asset payments to controlled wallet addresses, frequently changing them for each attack.
- Peel Chains and Intermediate Addresses: Funds are moved through multiple transactions to new addresses, often involving several VASPs, to obscure the asset trail.
- Mixers and Tumblers: These are used to conceal connections between sending and receiving addresses. CoinJoin transactions combine multiple payments into one, further obscuring origins.
- Anonymity-Enhanced Cryptocurrencies (AECs): While Bitcoin is most used, AECs like Monero are increasingly requested for their obfuscation capabilities. Criminals may charge extra for Bitcoin payments due to traceability concerns.
- Chain-Hopping and DeFi Protocols: Criminals convert Bitcoin to other virtual assets, often using DeFi protocols, to evade tracking. This includes converting into stablecoins before exchanging into fiat currency.
- Use of Centralised VASPs and High-Risk Jurisdictions: Criminals often cash out through VASPs in high-risk jurisdictions or those with weak AML/CFT controls.
- Payments to Criminal Partners and Infrastructure Hosts: Ransomware attackers also use virtual assets from their attacks to pay criminal partners and infrastructure service providers.
Use of Money Mules in Conversion to Fiat Currency
- Attackers use money mules with VASP accounts to convert proceeds into fiat currency.
- These accounts may be created with stolen or fake identities or belong to complicit parties.
- Money mules, often unrelated third parties, handle smaller value transfers in the final laundering stage, making them harder to identify.
Types of sectors that may be involved in ransomware financial flows
Financial Institutions
These act as intermediaries for ransomware victims or third parties acting on their behalf to transmit funds to a Virtual Asset Service Provider (VASP) for the purchase of virtual assets.
VASPs
Ransomware victims or their representatives use these providers to buy and transfer the virtual assets demanded by ransomware criminals.
Insurance Companies
These may cover and sometimes directly pay the ransom as a part of the victim’s cyber insurance policy.
Incident Response Companies
Hired by ransomware victims, these firms often handle negotiations with the attackers, purchase virtual assets from VASPs, and facilitate the payment of the ransom.
Cybersecurity Companies
These are tasked with protecting clients’ data, systems, networks, and devices from unauthorized and illegal access.
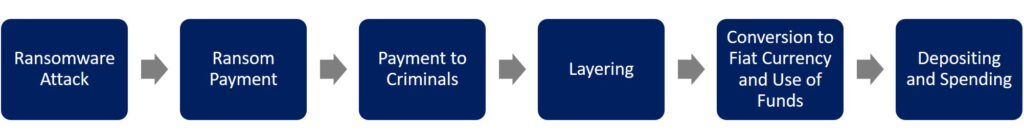
Ransomware Attack
Systems are attacked, disrupting the functioning of institutions, businesses, and organizations until a ransom is paid, usually demanded in Bitcoin.
Ransom Payment
Victims, or third parties acting on their behalf, such as incident response or cyber insurance companies, purchase the required virtual assets through a VASP, using wire transfer, automated clearinghouse, or credit card.
Payment to Criminals
The ransom payment is then transferred from a wallet hosted at a VASP to the perpetrator’s unhosted wallet, which is controlled by the ransomware criminal or a mule. This wallet is typically outside the jurisdiction of the attack and uncooperative with law enforcement agencies (LEAs) or financial intelligence units (FIUs).
Layering
Criminals employ various methods to layer the transactions, potentially involving multiple transfers to different addresses to disguise the link to the original crime.
Conversion to Fiat Currency and Use of Funds
Ransomware criminals often use VASPs located in different jurisdictions to convert virtual assets to fiat currency. They might also keep the funds in unhosted wallets for extended periods or use them to pay associates involved in the ransomware scheme.
Depositing and Spending
Eventually, criminals deposit, invest, or spend their illicit proceeds, further integrating them into the legitimate financial system.
Red Flags
Banks/Other Financial and Payment Institutions
Outgoing Payments:
- Wire transfers to firms specializing in ransomware remediation.
- Unusual wire transfers from insurance companies linked to ransomware.
- High volume of transactions to multiple VASP accounts.
Client Behavior:
- Self-reporting of a ransomware attack or payment.
- Payment descriptions with words like “ransom” or names of ransomware groups.
External Information:
- Open-source data on ransomware attacks involving clients.
Virtual Asset Service Providers (VASPs)
When Identifying Ransomware Victim Payment
Transaction Characteristics:
- Requests by incident response firms or insurance companies to buy virtual assets on behalf of a third party.
- Customers stating the purpose of buying virtual assets is for ransomware payment.
- Sudden, unusual transactions by customers with no history of virtual asset activity.
- Customers increasing account limits for sending to third parties.
- Anxious or impatient behavior regarding transaction times.
- Purchases or transfers of anonymity-enhancing cryptocurrencies.
Account Behavior:
- New customers immediately transferring the entire balance to a single address.
- Payments to VASPs in high-risk jurisdictions.
Identifying Ransomware Payment Receipt/Criminal Account
Account Activity:
- Inactivity following an initial large transfer.
- Immediate withdrawals after converting to virtual assets.
- Sending virtual assets to wallets tied to ransomware.
Transaction Patterns:
- Use of a VASP in a high-risk jurisdiction.
- Transfers to mixing services.
- Transactions with anonymity-enhancing cryptocurrencies.
Customer Behavior and Details:
- Use of encrypted networks or high-privacy email accounts (e.g., ProtonMail).
- Inconsistent identification details or attempts at false identity.
- Multiple accounts linked to the same contact details.
- Use of a VPN.
- Syntax not matching customer demographic.
- Suspicious verification information, such as photographs of data on a computer screen.
Source:
https://www.fatf-gafi.org/en/publications/Methodsandtrends/countering-ransomware-financing.html